IBM Cloud Pak® for Security provides a platform to quickly integrate your existing security tools and generate deeper insights into threats across hybrid, multicloud environments. The following diagram illustrates a high-level overview of IBM Cloud Pak for Security.
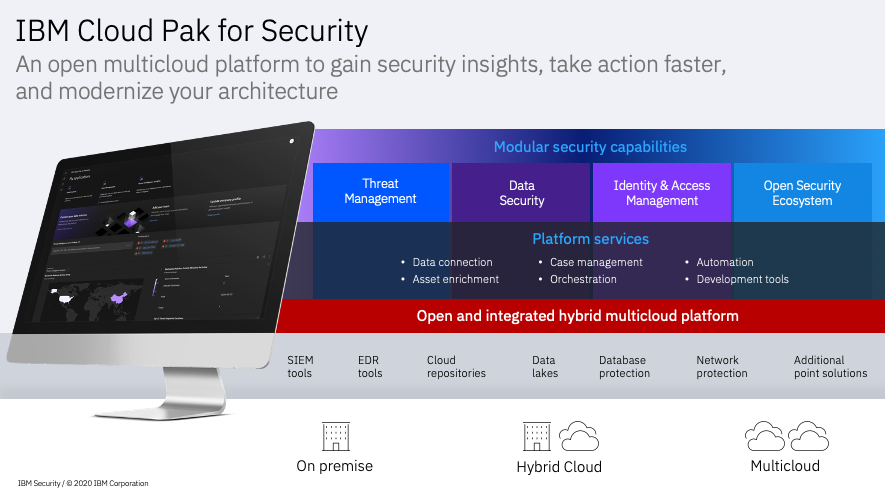
The Cloud Pak for Security platform uses an infrastructure-independent common operating environment that can be installed and run anywhere. It comprises containerized software pre-integrated with Red Hat® OpenShift® Container Platform, which is trusted and certified by thousands of organizations around the world.
Cloud Pak for Security can connect disparate data sources - to uncover hidden threats and make better risk-based decisions - while the data stays where it is. By using open standards and IBM innovations, Cloud Pak for Security can securely access IBM and third-party tools to search for threat indicators across any cloud or on-premises location. Connect your workflows with a unified interface so you can respond faster to security incidents. Use Cloud Pak for Security to orchestrate and automate your security response so that you can better prioritize your team's time.
IBM Cloud Pak for Security V1.6.0 offering includes the following applications:
IBM Security Data Explorer
IBM® Security Data Explorer is a platform application that enables the public sector to do federated search and investigation across hybrid and multicloud environment in a single interface and workflow. Data Explorer enables users to complete investigations in a timely manner without compromising visibility. Core underlying services and capabilities include:
- Federated data search to unite silos of security data and provide complete visibility across security solutions (e.g., security information and event management, endpoint detection and response, data lake), and cloud infrastructures (e.g., Azure, Amazon Web Services (AWS))
- Single, unified interface and workflow to investigate threats and indicators of compromise into user-selected data sources
- In-context data enhancements from connected assets and risk data sources and IBM® Security Threat Intelligence Insights
- Workflows to track, append, create security cases from the native platform case management system
IBM Security Threat Intelligence Insights
IBM® Security Threat Intelligence Insights is an application that delivers unique, actionable and timely threat intelligence. The application provides almost all of the functions that IBM® X-Force® Exchange provides:
- IBM-derived threat intelligence across threat activity, threat groups, malware and industries
- Continuous and automated “am I affected” searches across connected data sources to proactively identify your most relevant threats
- Analytical and adaptive threat-scoring to help prioritize threats for further investigation and response
IBM Security Case Management
IBM® Security Case Management for IBM Cloud Pak for Security provides organizations with the ability to track, manage and resolve cybersecurity incidents. With IBM Security Case Management, Security and public sector IT teams can collaborate across their agency or organization to rapidly and successfully respond to incidents. Case Management is a subset of the IBM® Security Orchestration & Automation application and is available without an extra license on IBM Cloud Pak for Security.
IBM Security Orchestration & Automation
IBM® Security Orchestration & Automation requires a license and is available as a stand-alone virtual appliance or as an application that is fully integrated in IBM Cloud Pak for Security. IBM Security Orchestration & Automation provides the following benefits:
- Create response plans that are based on industry standards and best practices.
- Integrate more easily with security and IT tools and orchestrate responses to events and incidents
- Collaborate across a public sector agency or organization, equipping various stakeholders with the tools to fulfill their roles and tasks as part of an incident response effort
If you have an Orchestration & Automation license, you can choose between the stand-alone version on a virtual appliance, or the application on Cloud Pak for Security:
- The stand-alone virtual appliance version provides the full feature set of IBM® Resilient® Security Orchestration, Automation and Response (SOAR) Platform
- The application that is integrated on Cloud Pak for Security provides most, but not all, of the IBM Resilient Security Orchestration, Automation, and Response Platform feature set
QRadar Security Intelligence Platform
IBM® QRadar® Security Intelligence Platform is offered as an on-premises solution and delivers intelligent security analytics, enabling visibility, detection and investigation for a wide range of known and unknown threats. Event analytics ingest, parse, normalize, correlate and analyze log and event data to detect indicators of threats. Event analytics also identify anomalous activities, automatically connect related threat activity and alert security teams to potential threats. Flow analytics collect, extract and normalize valuable network flow data and packet metadata to augment log-based security insights. Flow analytics also identify network and application-level threat activity, such as phishing, lateral movement and data exfiltration.
QRadar User Behavior Analytics
QRadar User Behavior Analytics (UBA) is a tool for detecting insider threats in your organization. UBA, used with the existing data in your QRadar system, can help you generate new insights around users and user risk.
IBM Security Risk Manager (Beta)
IBM® Security Risk Manager (Beta) for Cloud Pak for Security is an application that automatically collects, correlates and contextualizes risk insights across the IT and security ecosystem of your agency or organization. These risk insights are presented in a consumable dashboard to prioritize and remediate security risks. Risk Manager (Beta) provides the following key features:
- Unified view of disparate security risk metrics from multiple vectors, such as data, identity and infrastructure that helps risk prioritization in the public sector.
- Standard risk scoring framework for consistent and common risk definition that is easily understood by all stakeholders.
- Risk remediation management by using workflow management systems.
IBM Security Threat Investigator (Beta)
IBM® Security Threat Investigator (Beta) automatically analyzes and investigates cases to help you make more informed decisions. By showing potential threats and the assets that are impacted, Threat Investigator (Beta) can help determine the criticality of exposure, how many systems are at risk, and the level of remediation effort that is required. By viewing the historical timeline of threats within your agency or organization, you can better understand dwell times and the stage of the threat.