Digital Design, Technology, Tips and How-Tos, Uncategorized
If you’re fairly new to Autodesk Revit and looking for ways to quickly get up to speed, Autodesk put together a great webinar that offers tips and tricks to get the most out of your user experience. Topics included:
• How does it differ from AutoCAD?
• What do I need to know to get started?
• What are some best practices for working in Revit?
• What are families and how do I use them?
• Where to learn more and how to get support when problems happen
Big Data, Cloud Computing, Internet of Things, Technology
IoT Demo: Here
Blog Part 1: Setting the Stage
Blog Part 2: Architecting the Scene
Cybersecurity, IT Perspective, News, Technology
Ransomware is quickly becoming the favored means for criminals to extract a profit from unsuspecting villains – most notably in the public sector. Throughout 2017 ransomware grabbed the headlines – WannaCry, Petya, etc. – both of which targeted government agencies. When they succeed the implications can be serious.
Cybersecurity, Infrastructure, Technology, Uncategorized
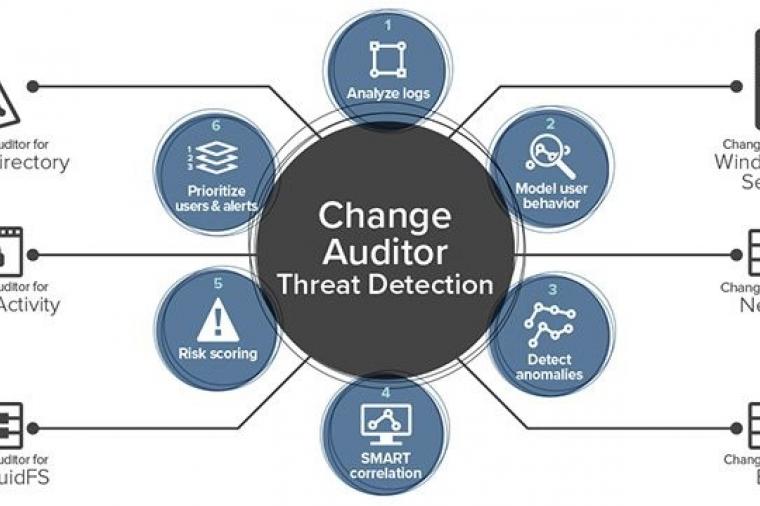
Microsoft Active Directory is a critical tool that helps system administrators manage user privileges and secure their IT infrastructure, yet Active Directory presents several security challenges. Most problematic is that Active Directory’s attack surface is huge. Targets for attack include every domain name user account, admin and security group, domain controller, backup, admin workstation, and admin delegations and privileges. If any one of these targets is compromised, your entire Active Directory can be compromised too.
The Threats
Cybersecurity, Infrastructure, IT Perspective, Technology, Uncategorized
Microsoft Active Directory is a critical tool that helps system administrators manage user privileges and secure their IT infrastructure, yet Active Directory presents several security challenges. Most problematic is that Active Directory’s attack surface is huge. Targets for attack include every domain name user account, admin and security group, domain controller, backup, admin workstation, and admin delegations and privileges. If any one of these targets is compromised, your entire Active Directory can be compromised too.
The Threats
Cybersecurity, Technology
Ransomware tops today’s list of security concerns for governments, and no agency is immune. Just look at the statistics:
• Cook County, Chicago was a victim of last year’s WannaCry ransomware attack.
• St. Louis Public Library was hit with ransomware, demanding $35,000 in Bitcoin.
• Bingham County, Idaho paid out #3,000 in ransomware to restore its servers.