Breakthrough in Ransomware Prevention is Good News for Government Agencies

Ransomware is quickly becoming the favored means for criminals to extract a profit from unsuspecting villains – most notably in the public sector. Throughout 2017 ransomware grabbed the headlines – WannaCry, Petya, etc. – both of which targeted government agencies. When they succeed the implications can be serious. Licking County in Ohio fell victim to a ransomware attack that regressed its operations 25 years as personnel were forced to work offline.
Ransomware works by blocking access to a system or its data via encryption, until a certain amount of money is paid by the victim. Ransomware is distributed through highly targeted phishing emails, social engineering schemes, watering hole attacks, etc. all of which are delivered by commercial malware kits that can be purchased by any criminal on the dark web.
It’s Not Just Consumers Anymore
Ransomware was often a consumer problem, criminals would target unwitting home computers and block access to family photos or files, in return for a few hundred dollars in ransom. But that’s not the case anymore.
Cybercriminals are starting to recognize that if consumers or one-off business users are willing to pay $300 to $500 to unlock run-of-the-mill data on a single endpoint, government agencies and other organizations would likely be willing to pay much more for mission-critical data, or to unlock an entire fleet of endpoints held hostage in a single instance.
Think Your Backup Tapes Have You Covered?
Government agencies often don’t perceive the threat because, after all, they have everything backed up for easy recovery should the worst happen.
But incomplete backups, especially those that skip certain endpoints like BYOD or remote workers, make them vulnerable. Plus, new ransomware variants contain code that can attack unmapped network drives and even cloud-stored assets that aren’t in your average backup routines. Even more worrisome is that ransomware can now target backup files as part of their attack patterns.
More recently, ransomware coders have stepped up their release of innovative and dastardly features. For example, malicious Microsoft macros and JavaScript file attachments are used to spread ransomware to avoid detection.
Where Do You Go from Here?
Clearly backups are important, but they’re not the panacea. This whitepaper, Ransomware, A Growing Enterprise Threat, CrowdStrike (a DLT partner) offers tips and approaches that can help protect your agency from attack.
CrowdStrike notes that conventional signature-based endpoint protection has already proven itself inadequate at detecting ransomware before it strikes. Additional measures such as whitelisting, Indicators of Compromise (IOCs) or machine learning can each add a nominal degree of improvement over signature-based detection, however they each have their own limitations. For example, in the case of fileless and zero-day ransomware (one that takes advantage of a hole in software security), all those countermeasures would prove unreliable in detecting or preventing attacks. Furthermore, relying on IOCs, which by definition can only be detected after a compromise has occurred, typically end up alerting IT to the attack after it’s too late to make a difference -- in most instances, by the time firm IOCs present themselves, the ransomware has already encrypted its target data.
CrowdStrike’s approach is different. It combines multiple methods into a powerful and integrated approach that protects endpoints more effectively against the menace of ransomware. Its solution, Falcon Prevent, uses an array of complementary prevention and detection methods.
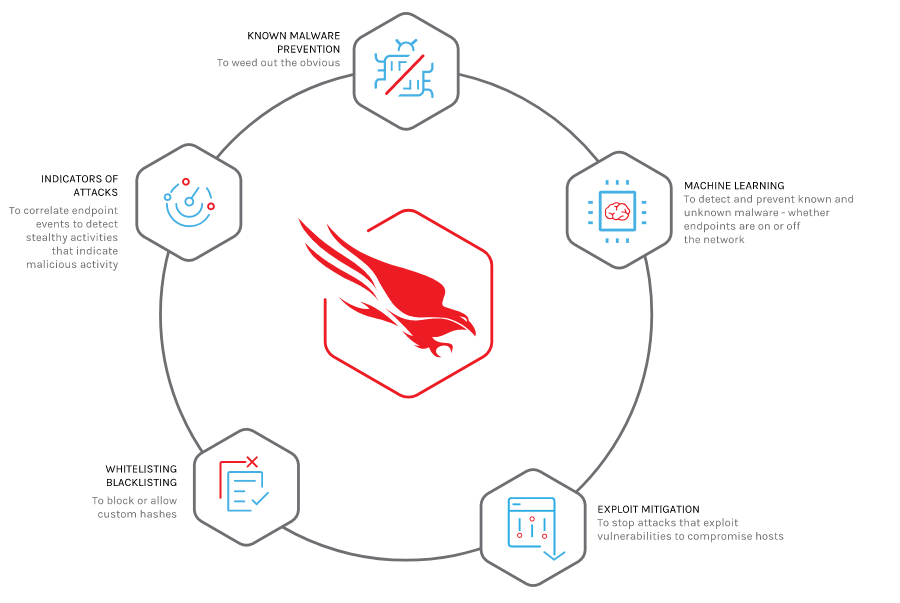
Here’s what it can do:
• Block known ransomware to weed out common threats
• Exploit blocking to stop the execution and spread of ransomware via unpatched vulnerabilities
• Machine learning for detection of previously unknown, or zero-day ransomware
• Uses indicators of attack (IOAs) to identify and block additional unknown ransomware in the early stages of an attack before it fully executes and inflicts damage
The big breakthrough here for ransomware detection are IOAs. With IOAs, Falcon Prevent looks for early warning signs that an attack may be underway. Those signs can include code execution, attempts at being stealthy, and lateral movement, to name a few.
In addition, IOAs provide a reliable way to prevent ransomware from deleting backups. This gives users the ability to restore encrypted files, even if file encryption began before the ransomware was stopped.
That’s reason enough for Falcon Prevent to win achieve a 100% rating for detecting known and unknown malware samples with a false positive rate of 0% in it first public test – and, achieve “Visionary” status in Gartner’s MQ for endpoint protection.


































