Digital Design
Over the last decade, BIM has radically transformed design and construction projects and is seeing increased adoption in the U.S. government sector.
Digital Design
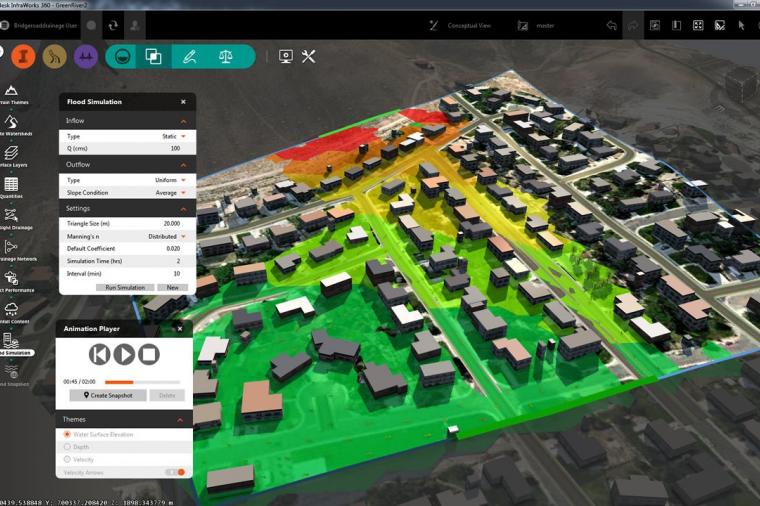
As global temperatures rise, extreme downpours can result in flash floods that put a catastrophic strain on U.S. infrastructure. In fact, a new study from Nature Climate Change and reported by The Guardian, suggests that by the century’s end, storms that now occur once a season (like the Louisiana flood of 2016) could happen five times a season – a 400% increase.
Cybersecurity
Late last year, the government’s Commission on Enhancing National Cybersecurity published a detailed report, at President Obama’s request, to provide short- and long-term recommendations to strengthen cybersecurity in the public and private sector (you can read the full report on the NIST website).
Digital Design
As a government user of Autodesk software, you may be aware that Autodesk is changing its licensing policy. Effective, January 31st 2017, the previous government extension will end and users will no longer be able to purchase perpetual licenses. You can read more about the specifics of the changes here.
Data
Can you afford for your team to lose eight hours a day? According to the 2016 State of Data Center Architecture and Monitoring and Management report by ActualTech Media in partnership with my company, SolarWinds, that’s precisely what is happening to today’s IT administrators when they try to identify the root cause of a virtualization performance problem. And that doesn’t even take into account the time required to remediate it.
Digital Design
Keeping track of all the documents involved in any construction or infrastructure project can be quite a headache. RFIs, design changes, estimates, mark-ups, approvals, and more, not forgetting the many-to-many relationships involved in the process. Sub-contractors are on and off the construction site, changes, issues, and requests are sent back and forth, new document sets are created and versions are updated.