Cybersecurity
Getting to know the “enemy with no face” is critical to winning the cyber war. In fact, it’s the tagline from the U.S. Army’s latest cyber warrior recruitment ad. Yet, one of the biggest challenges to doing so is that most organizations have zero visibility into a significant percentage of the endpoints on their network. That’s because they are either not managed (BYOD, guest, and IoT), have disabled or broken agents, or aren’t detected by periodic scans.
Cybersecurity
From veterans to tax payers, contractors to military personnel, the U.S. government is one of the world’s largest harbors of personally identifiable information (PII). Year after year of security breaches has done nothing but destroy public trust in the government’s ability to protect PII about citizens, employees, and contractors.
Cybersecurity
I bet there was a time you loved your security information and event management (SIEM) system. This central location for managing all the security events on your network. But, as good as it may seem, many IT organizations have a love/hate relationship with their SIEM.
Cybersecurity
As government officials begin investigation of the Equifax breach that exposed the sensitive information of 143 million people, what does the breach mean for agencies themselves? After all, the U.S. government stores far more sensitive data than the private sector, and often stores it on older, more vulnerable systems.
Cybersecurity
Hackers are ruthless in their persistence and fortitude. It can take weeks or months for them to gather intelligence on your IT vulnerabilities, penetrate your network, and exfiltrate your precious data. But they know, and statistics prove this, that, for the most part, their victims have no idea that their network infrastructure is under attack – until it’s too late.
Cybersecurity
Another month, another regulation deadline to comply with. But this time, it’s defense contractors who are in the hot seat.
To safeguard defense information in non-federal systems and organizations, U.S. defense contractors and soon all federal agencies, must meet the DFARS 7012 mandate and implement all of the requirements of NIST Special Publication 800-171 Protecting Controlled Unclassified Information (CUI).
Cybersecurity
Securing government networks and systems takes a village. Keeping pace with attacks and shortage of security talent has driven security operations to pool data resources and orchestrate actions across vendors, open source projects, and internal development efforts. It’s a community effort. Sharing threat information and codifying procedures to better fend off the enemy with no face. This kind of intel also improves detection efforts and response through collaboration across systems.
Cybersecurity
Time is running out for federal contractors to comply with the Federal Controlled Unclassified Information (CUI) Program.
What does the CUI Program mean to contractors?
As of December 31, 2017, all federal contracts will require that businesses contracting with the federal government must comply with the Federal CUI rule (32 CFR Part 2002) which strives to eliminate ad-hoc policies and markings that agencies and departments apply to unclassified information that requires safeguarding or dissemination controls.
Cybersecurity
It’s clear that smart technologies and the Internet of Things (IoT) are the future of our communities. But, is your agency ready for the billions – soon to be trillions – of sensors and devices connected to one another that will transform our society?
The risks of a breach or attack, particularly to vulnerable network endpoints, are worrying and costly. Impacts include:
Cybersecurity
After hearing Congressman Langevin and NSA speak at the ICIT Annual Forum event it became obvious that the “Enemy with No Face” is getting in to our networks and what they want is our data. FinalCode is purpose built to protect files with encryption and Information Rights Management (IRM), sometimes called Enterprise Digital Rights Management (EDRM).
Cybersecurity
“The enemy with no face”. No, it’s not the latest Dwayne “The Rock” Johnson Hollywood action movie, but the tagline from the U.S. Army’s latest cyber warrior recruitment ad.
Cybersecurity
Two years on from the massive Office of Personnel Management (OPM) data breach, current and former officials have concluded that the greatest fallout from the hack was not the loss of documents and personal identifiable information, but to the government’s reputation, reports NextGov.
Cybersecurity
Metadata. It’s not a word that springs to mind when you think about detecting and stopping attacks on your networks and endpoints. If you’re investigating an attack you probably pull logs files and Netflow data to try and make sense of what’s going on. Nothing wrong with that. But as with all things cybersecurity, there’s always more you can do. And that’s where metadata comes in.
Cybersecurity
Although still in its infancy in the public sector, making the shift to DevOps methodologies is starting to catch on with many government agencies, including the U.S. Citizenship and Immigration Services, the EPA, and Nuclear Regulatory Commission.
As you may know, with DevOps, IT tasks and application deployment that would normally take months or years, now take weeks.
But Rome wasn’t built in a day.
Cybersecurity
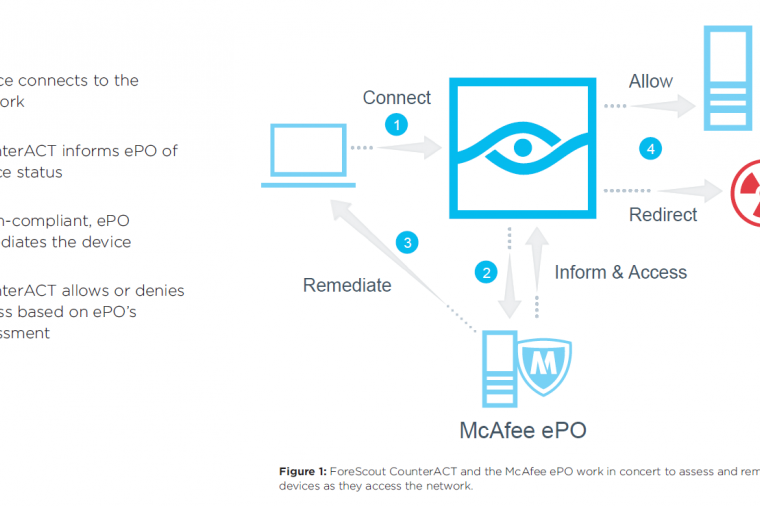
We all know that the Internet of Things (IoT) is here. But IT professionals responsible for enterprise communications networks aren’t exactly sure where IoT resides on their networks or whether these devices are secured. Rogue devices are everywhere (although not all are out to steal the blueprints to the Death Star) but according to a survey sponsored by ForeScout Technologies, only 30% are confident that they know what IoT devices are on their network.
Cybersecurity
Late last year, the government’s Commission on Enhancing National Cybersecurity published a detailed report, at President Obama’s request, to provide short- and long-term recommendations to strengthen cybersecurity in the public and private sector (you can read the full report on the NIST website).
Cybersecurity
The concepts of threat hunting and threat intelligence went mainstream in 2016 bringing with it a whole new paradigm to threat mitigation and cybersecurity. But what is threat hunting and what use cases does it serve?
Cybersecurity
Got breach fatigue yet? Yes, it’s been another bad year for computer security. 2016 saw the announcement of the biggest breach ever – the Myspace hack. But, that was quickly eclipsed by the September Yahoo data breach which resulted in the exfiltration of extensive account information, included passwords, from 500 million users.
Cybersecurity
When your agency detects a network attack, you need to act fast to understand what’s going on. But getting the insights and analytics you need takes time and often doesn’t trace threats back to the source.
Cybersecurity
Security Information Event Management (SIEM) tools have been around for quite some time. SIEMs are great for aggregating log files, parsing them, and using real-time correlation rules to spot security incidents. But more advanced incidents can evade detection by your SIEM. Finding those evasive threats becomes a lot easier if you employ threat hunting.
Cybersecurity
Data dissemination and file sharing between agencies and law enforcement authorities is a natural part of government business. But what happens when those files leave the security of domain-controlled network drives and content management systems?